
Carding is the prince of cybercrimes. It involves trafficking with stolen payment card data: card number, expiration date, and holder’s name. Those who purchase it can use the details to buy everything online with the legit owner’s money. EmpireMarket is a dark web platform that offers to sell this data (in addition to counterfeit banknotes, arms, and fake documents).
The Bazaar does go online and offline periodically for security reasons. The managers now write on the front page that other cyber-criminals have been targeting them “for more than two weeks”. They announce these hackers “have only gained part of the control” of the platform. So, the administrators ask for financial help “from every user” to face the current problems: a donation worth $ 30 in Bitcoin cryptocurrency (aiming “to buy more servers“).
Before the attack, American Express, Mastercard, and Visa payment cards were offered for sale on the website. A Prepaid Card with a balance of 3100 $ cost 110 $ if American Express, 114 $ if Mastercard, 109 $ if Visa.

EmpireMarket – Credit Cards Prices
EmpireMarket, a cyber investigation
Summary of contents
Purchasing method: Escrow
The purchasing method was detailed and explained. The customer needed to pay, and then a vendor operating on the website would have sent him the stolen payment card details. Nevertheless, the risk of scams is always high: paying without receiving the data. We are on the dark web without contract, authority, or possibility of claims. For this reason, the Escrow method allegedly guaranteed the agreement.
“What is Escrow?
- The buyer sends money to Escrow during the checkout process. (It’s active with every trade)
- The vendor receives a notification about money in Escrow.
- The vendor will send the order/product to the buyer.
- The buyer checks the product and releases money from Escrow to the vendor if it is as described.
- Trade is finished, and all personal details are removed.”
No personal details of the vendor were available on the website, as the activity is highly illegal. However, some trails can help to discover more.

Escrow Payment Method
A clue: the email domain Airmail.cc
At the bottom of EmpireMarket’s homepage, “support ” was a section. It would have helped customers who faced technical issues. But it also contained a clue for our research, an active email address: empiresupport@airmail.cc.
The airmail.cc email service is not a popular provider like Gmail, Yahoo, or Outlook. Yet, its domain links to a corresponding website.
The Airmail.cc front page displays a short message: “Airmail is an invite-only Email server focused toward professionals and Email enthusiasts. To report abuse please Email abuse [at] Airmail.cc.”
Thus, it is a provider offering an email service not associated solely with Empire Market fraudsters’ activities.
Shodan: the internet connections
Using an OSINT tool named Shodan, we can add some information. Shodan is “a search engine for Internet-connected devices” (shodan.io).
A standard search engine (Google, Bing) looks for relationships based on the contents on the web (the service displaying web pages). You insert a word or sentence and see the pages corresponding to the searched content.
Instead, Shodan searches the connections on the internet, which is the network that links computers and servers. Every activity on the net leaves a trail, the IP address: a sequence of digits identifying a unique source of connection and nearly impossible to replicate. When searching for a website domain on Shodan, the search engine shows the devices’ data (primarily servers) connected to the queried name: first, the Ip address and its location.
Looking for the connection with Airmail.cc, the search engine Shodan displayed three results (last visited on the 20th of April). The first is an Ip address located in Belgrade (Serbia), the second is in Vietnam, and the third is an IP address in New York (US). The three locations are far away, one from the other.
Indeed, the servers can be located everywhere globally, although the physical person behind the connection is in another area. A hacker in the US can use remote servers located in Eastern Europe. In this case, despite Serbian and Vietnamese Ips not showing links at first glance, New York Ip does.
The hacker EdmondMajor
By clicking on the New York IP address, we are redirected to a webpage (http://edmond.bz/) of a self-defined hacker (grey hat?): EdmondMajor. He described himself as “Highly interested in cybersecurity”. The webpage links to another website (http://www.edmondmajor.com/), where you can read a manifesto: “The Conscience of a Hacker”. He writes: “I am a hacker, enter my world (…)Yes, I am a criminal. My crime is that of curiosity.”

Edmond Major’s webpage
He offers services for companies: “Phishing your employees”, “Un-Hack/De-Malware Your Servers”, and “Research or Spy on Your Competition” (among others).
On the webpage edmond.bz, he provides a contact email: em3@airmail.cc. He chose to set up an email account with Airmail.cc, which seems a secure way to communicate: a cybersecurity expert selected it. It could explain its use also by the highly illegal platform EmpireMarket.
Waybackmachine: what Airmail.cc looked like in the past
Airmail.cc email works, but the corresponding website doesn’t contain relevant information. Now. What about in the past?
Waybackmachine (archive.org) is an Internet archive. It stores web pages published at a specific date, allowing users to see how websites looked in previous years.
From 14th September 2018 until 25th November 2021, the homepage of “airmail.cc” redirected to another website: “ovo.sc”. “Sc” is the internet country code for Seychelles. Ovo is the name of a group, as explained on the website “ovo.sc” (still active).
Waybackmachine: OvO welcome meesage
It is “a global collective of service providers and provided services. Its members share knowledge, resources, and support with the aim of building sustainable, independent online businesses”.
“OvO’s network hosts several free speech and cryptocurrency services. To report abuse, email abuse // ovo.sc and include all applicable logs and evidence.”
Although now Airmail.cc no longer links to OvO, we can infer there has been a connection between the two services.
Panama papers: an offshore company
The signature under the message on the front page ovo.sc reports the “OvO Systems Ltd” group’s address: “Suite 9, Ansuya Estate, Revolution Avenue Mahe Seychelles”.
The same direction is contained in the “Panama Papers“, which are 11.5 million leaked financial information documents for more than 210 thousand offshore entities. They have been published since 2016 by the International Consortium of Investigative Journalists (ICIJ). Offshore entities are subjects (primarily companies) registered in foreign (often tax-favourable) jurisdictions.
According to the Panama Papers, two companies were registered at the Ovo Systems Ltd direction in the past: “Enterprise Solutions Ltd” (now inactive) and “Professional Consulting Services Ltd” (inactive as well).
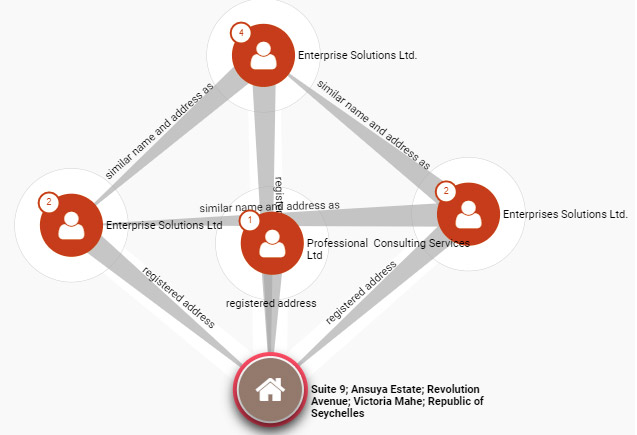
Panama Papers: companies at OvO address
Currently, the company “Fidelity Corporate Services (Seychelles) Ltd” is registered there. It is a specialist offshore company formation agent. They provide company registration services in the country.
A company registered in Seychelles doesn’t necessarily be fraudulent. As the ICIJ alerts, “there are legitimate uses for offshore companies and trusts”.
MyIP: domains connected to Airmail.cc
There is another helpful tool for investigating a domain. MyIp.ms is an online database “that helps you find out who hosts a website”. Suppose you type a website name (Airmail.cc in our case). In that case, MyIp shows where the server hosting the site is located and, in addition, the other domains connected.
There are several websites related to Airmail.cc.
a) Cockbox.org, a “Bitcoin VPS provider”
Cockbox.org is one result. It is defined as a “Bitcoin VPS provider”. VPS is the acronym for a virtual private server: an application running in your system and working as a server.
Cockbox is the organization offering this “virtual machine” as a service. According to the website, “Cockbox’s servers are in Bucharest, Romania”.
The payments are accepted in the cryptocurrencies Bitcoin or Monero. A message at the bottom of the page indicates: “Service provided super serious by OvO Systems Ltd.”

Cockbox.org frontpage
b) Cock.li, email services
Cock.li is another result (the website’s logo is the same as cockbox.org). It provides “stable Email services” for professionals. Indeed, it is an email provider privacy-oriented and runs with encryption. It “allows registration and usage using Tor and other privacy services”.
At the bottom of the page is written: “The service is provided for fun by OvO Systems Ltd”. The service manager is the American Vincent Canfield (living in Romania, as per his Twitter profile description). In April 2021, he tweeted that they closed the registration to the service as they had reached 1 million users.

Cock.li frontpage
The provider Cock.li has several distinct domains registered and listed on the homepage. Among them, the same Airmail.cc. In 2015, Canfield explained: “the “invite-only” bit on the front page of Airmail.cc is a farce, Airmail.cc is a publicly-registerable domain name available here: cock.li”.
On the homepage of Cock.li, they want to specify that they are “as transparent as possible”. “To accomplish this Cock.li publishes communication with law enforcement including or regarding a successful demand or order for user information.” The communications between cock.li and authorities (emails and phone calls) are shared on the website.
Cock.li legal issues
In multiple cases, distinct US authorities contacted cock.li to get information on suspicious clients or criminals using the services provided by the organisation. American agencies also delivered some subpoenas to Vincent Canfield, and in some cases, they seized his hard drives. Several investigations were related to child exploitation.
In January 2017, Canfield wrote: “The last preservation of records request received by the US government was immediately followed by the seizure of cock.li’s hard drives by the hands of the US Government”. Indeed, he informed that the US Customs and Border Protection (CBP) seized all of his electronics when entering the United States.
It’s not the first legal issue faced by Canfield. In 2016, he wrote: “My friends, This evening, I was arrested by the Romanian Police. (…) I am being extradited to face a charge under Strafgesetzbuch section 86a, which bans, amongst other things, the use of “slogans of unconstitutional organisations”.
“For about three weeks, I displayed a JOKE on the front page of cock.li (…) that said “HITLER DID NOTHING WRONG”. I did this while the server was hosted in Germany, so I think this is what this is about. I’ve never been unironically racist in the entire history of the site, so this is the only thing I can come up with. (…) I’ve also been informed that my extradition is being expedited because I am scheduled to undergo investigative surgery. The prosecution office in the city of Zwickau believes I may have a surgically-implanted storage device. The SRI performed forensics on my storage devices in my apartment and did not find another copy of the cock.li data”.
Uses by intelligence services
However, the legal problems seem pretty old. As of April 2022, the website reports: “From 2017 to 9th April 2022, cock.li has not received:
- A gag order preventing the disclosure of a broad order for user metadata
- A gag order preventing the disclosure of a broad order for user data
- A gag order preventing the disclosure of a targeted order for user data
- A gag order preventing the disclosure of a targeted order for user metadata”.
Still, Canfield writes on the website that in the first quarter of 2022 cock.li received and responded to “two verified orders for user metadata enforceable in the jurisdiction of Seychelles on behalf of French authorities”.
Furthermore, according to the website Deepwebmarketsreview, in November 2019, the provider’s servers were taken offline, possibly due to a search warrant. There is no further information on that.
In April 2021, the FBI reported that “a number of SVR [Russian Foreign Intelligence Service] cyber personas use email services hosted on cock.li or related domains”. Canfield told the website Vice: “This is the first time I’ve heard for sure that Russian intelligence is using cock.li, but it’s not surprising, since the CIA uses it too”.
Cock.li donations
Cock.li relies on donations to survive, the homepage states. It also publishes an annual financial report. In the 2020 report, Canfield writes: “In the last year, cock.li has gone from being completely hosted in one country, to being geographically distributed within Eastern Europe. This change has brought long-term resilience to the site at the cost of speed and reliability. (…) Cock.li received a 1.5BTC donation in 2018 that is still funding the site today.”
2021 report hasn’t been published yet.
https://t.co/ZAZav0K4D5 have incorporated under the name “OvO Systems Ltd”! I can now join @RIPE_NCC , get an ASN, and do all sorts of fun stuff :^)
WE CORPORATE NOW MOTHERFUCKhttps://t.co/eWmtisd6LU
— Vincent Canfield (@gexcolo) October 7, 2018
MyIP and Shodan with Ovo.sc, another carding website
In 2018, Canfield tweeted that Cock.li and Cockbox “have incorporated on the new name “OvO Systems Ltd”.
According to Shodan’s research on ovo.sc (run on the 30th of March), the servers hosting Ovo Systems Ltd are reportedly located partly in Romania and partly in Seychelles. MyIp links these latter servers to a telecommunication company: “Flokinet Ltd“. Flokinet has an office in Iceland and one in Seychelles, according to the website flokinet.is. It offers hosting services, web design services and security consulting. It was “established in 2012 – Iceland, to provide a safe harbour for freedom of speech, free press and whistleblower projects”.
One of the Ip addresses connected with OVO and owned by Flokinet links to the website domain cardmafia.pw. This website’s description on hypestat.com states: “Russian carding forum, verified carding forum, altenen.com new domain”.
OvO Systems, a solution for cybercriminals
The cluster OvO Systems Ltd provides valuable services covering identities, messages, and connections online. So, hackers, fraudsters, and cyber criminals use it. The benefits (some of the services are free) are rewarded with conspicuous bitcoin donations.
This network could be fundamental, above all, right now. In February 2022, Russian authorities arrested six men active in selling stolen payment card data. (FSB, Russia’s domestic security service led another action with the same target in March 2020). According to the journalist Brian Krebs, carding platforms UniCC, Trump’s Dumps, Ferum Shop, and Sky-Fraud (among others) could be involved in this operation.

Russian Message for Trump Dumps users
According to the website Digitalshadow, now someone guesses the carding markets should move to Telegram for safe communications. Others argue that they should implement security in their procedures.
Behind some carding platforms (EmpireMarket, Cardmafia), we found offshore companies, anonymous email accounts, and privacy services. Identifying cybercriminals behind them is challenging, also for law enforcement agencies. The cluster OvO Systems could be a significant resource for carding fraudsters also in the future.








